
by Eagle Network Solutions | Jan 26, 2023 | Client Services, Our Services, Products, Tech Tips
From the Desk of Kaleb Jacob If you are an Eagle client, then you know that we are a one stop shop for most technology needs. We quote a lot of equipment for our clients including firewalls, switches, PC’s and laptops. We spend a lot of time researching, quoting and...

by Eagle Network Solutions | Oct 23, 2022 | Client Services, Our Services, Tech Tips
Today it is necessary, and I would argue crucial, to use multifactor (MFA) or 2-factor (2FA) authentication on important resources that you access such as banking sites or email. Most of you probably have the Microsoft Authenticator app or Google Authenticator on...
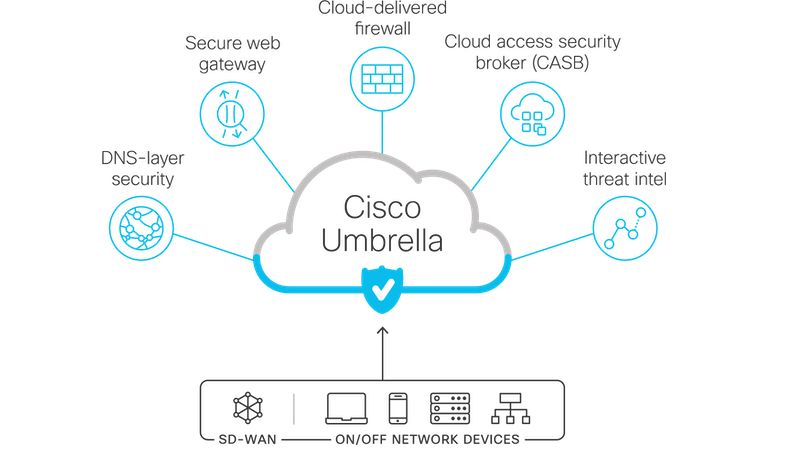
by Eagle Network Solutions | Jul 27, 2022 | Products, Tech Tips
By Thomas Begush – Service Technician II Would you like to prevent cyber-attacks from happening? Wouldn’t it be reassuring to have more visibility to what information is flowing into and out of your company’s network? Eagle Network Solutions has...

by Eagle Network Solutions | May 13, 2022 | Client Services, Tech Tips
When an employee leaves your business, what policies do you have in place to disable their access? If you don’t have a standard practice in place today, we recommend implementing a policy on this topic. From time to time, we see an associate continue to use a past...

by Eagle Network Solutions | May 12, 2022 | Client Services, Tech Tips
The I.T. landscape is constantly evolving. New threats and vulnerabilities emerge at a whiplash speed. When we started this business 18 years ago, support for businesses was predominantly break/fix. If something didn’t work, you phoned us to come and fix it. The...

by Eagle Network Solutions | May 11, 2022 | Tech Tips
From the Desk of Kaleb Jacob, Principal CEO Cloud solutions for data storage have opened up options for the modern business to store, share and collaborate with their company’s data. It can be convenient to drop a file in Dropbox or some other cloud product so you...







